Tisalabs Knowledge Base
Phishing remains a significant threat, necessitating proactive measures to assess organizational susceptibility. In this tutorial, guidance will be provided on executing a phishing campaign featuring a fake login page targeting Facebook credentials. By following these steps, a better understanding of the process and an enhancement of the organization's cybersecurity posture can be achieved.
To begin, a convincing landing page resembling the Facebook login interface needs to be crafted.
Step 1: Development of Fake Facebook Login Page The creation of a phishing website mirroring the Facebook login page will effectively deceive users.
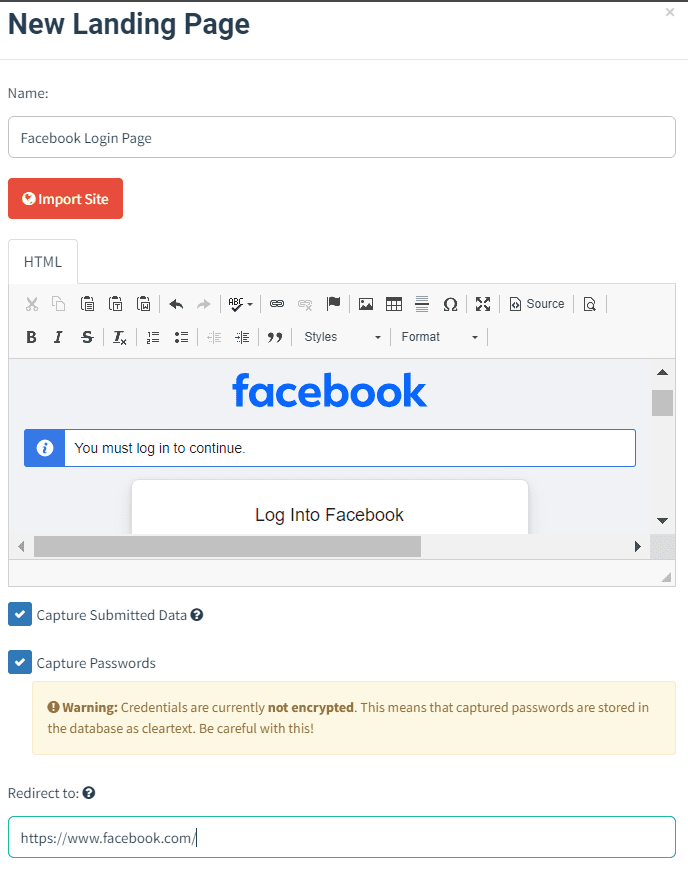
then once we capture the credentials it will redirect them to the main page of Facebook.
Step 2: Crafting the Email Template Next, an email template will be designed that prompts users to take action by clicking on a link leading to the fake login page.
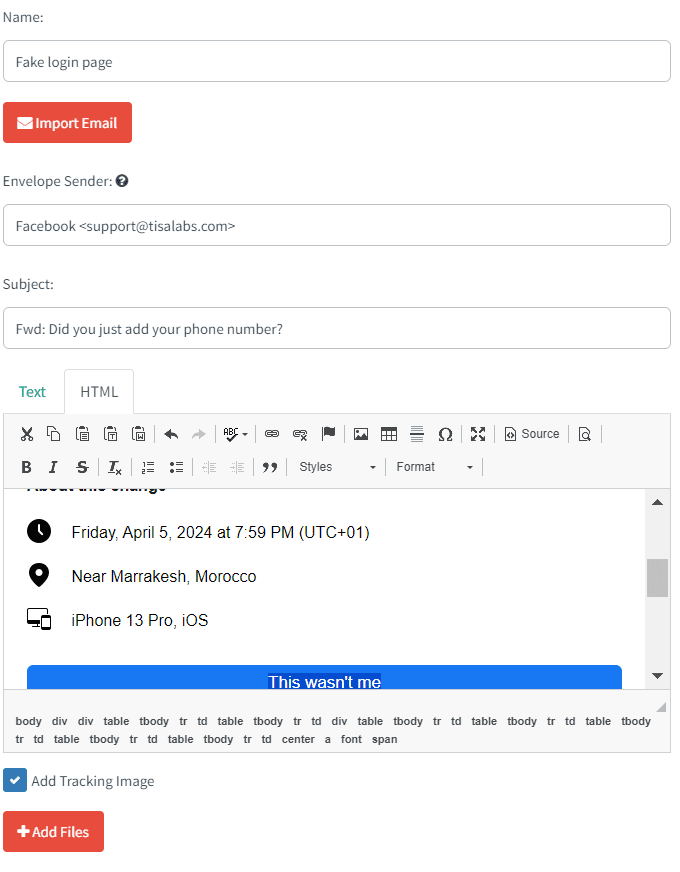
Step 3: Crafting Email Content Persuasive email content, such as notifications to users regarding suspicious activity on their Facebook account, will be composed.
With all elements prepared, it's time for the phishing campaign to be launched.
Step 1: Launching the Campaign The campaign will be initiated in the phishing simulation tool, with configurations made as needed.
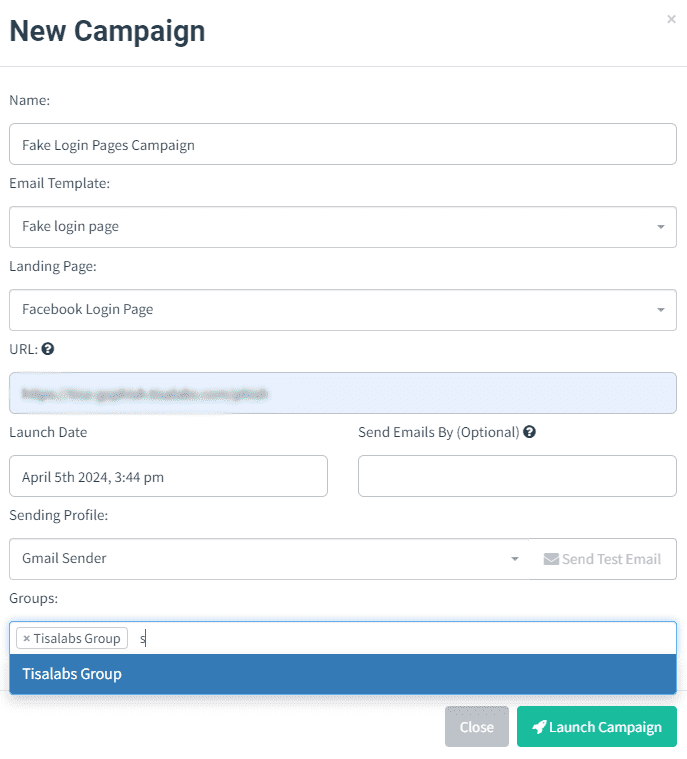
Step 2: Monitoring Campaign Progress Campaign progress will be monitored from the dashboard, with user interactions and email open rates being tracked.
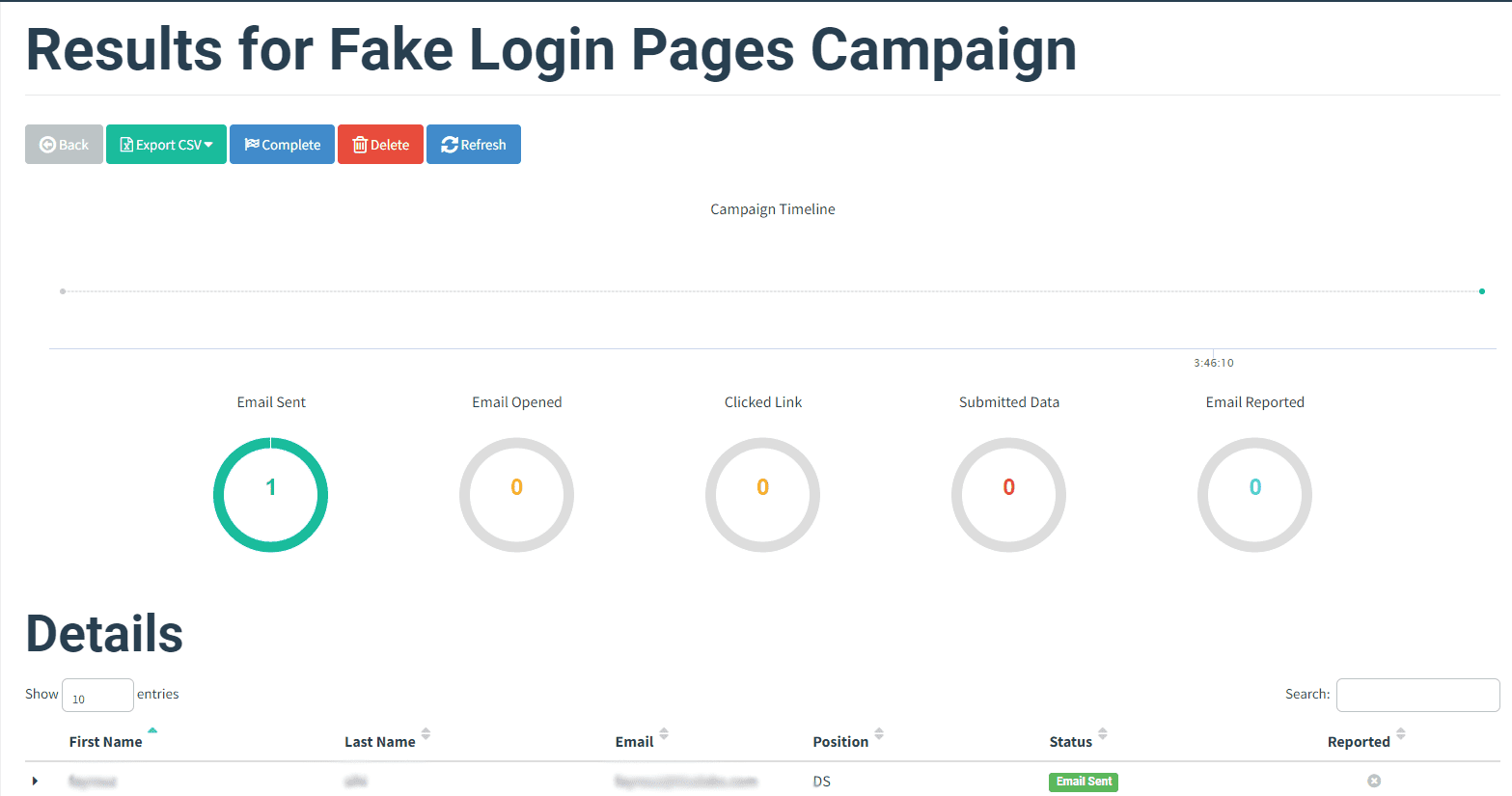
The outcomes of the phishing campaign will be reviewed to evaluate its effectiveness.
Step 1: Email and Landing Page Appearance Inspection of how the phishing email appears in recipients' inboxes and review of the landing page's authenticity will be conducted.
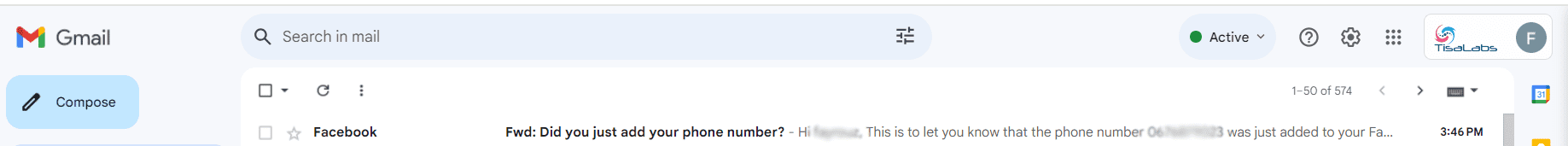
also this the content of the email that the target user gets:
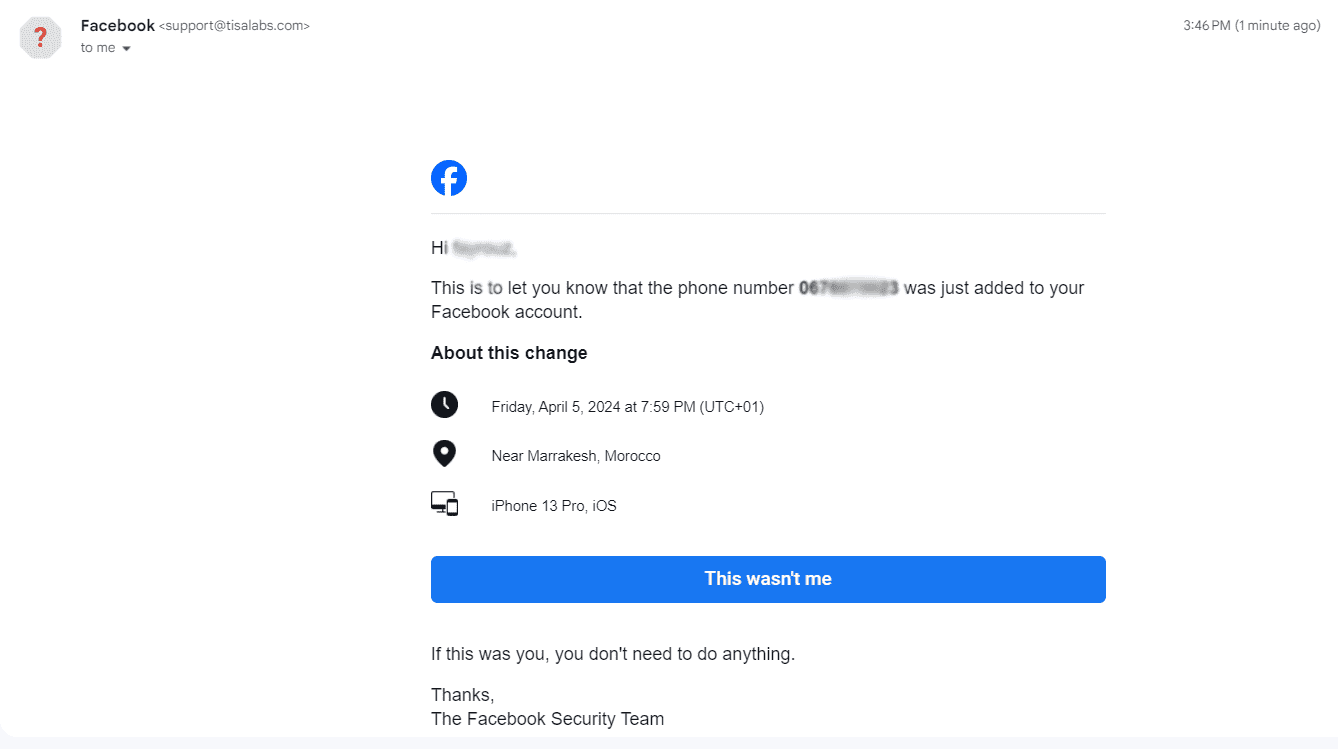
Step 2: Victim Interaction Examination of user interactions, including attempts to login on the fake Facebook page, will be performed.
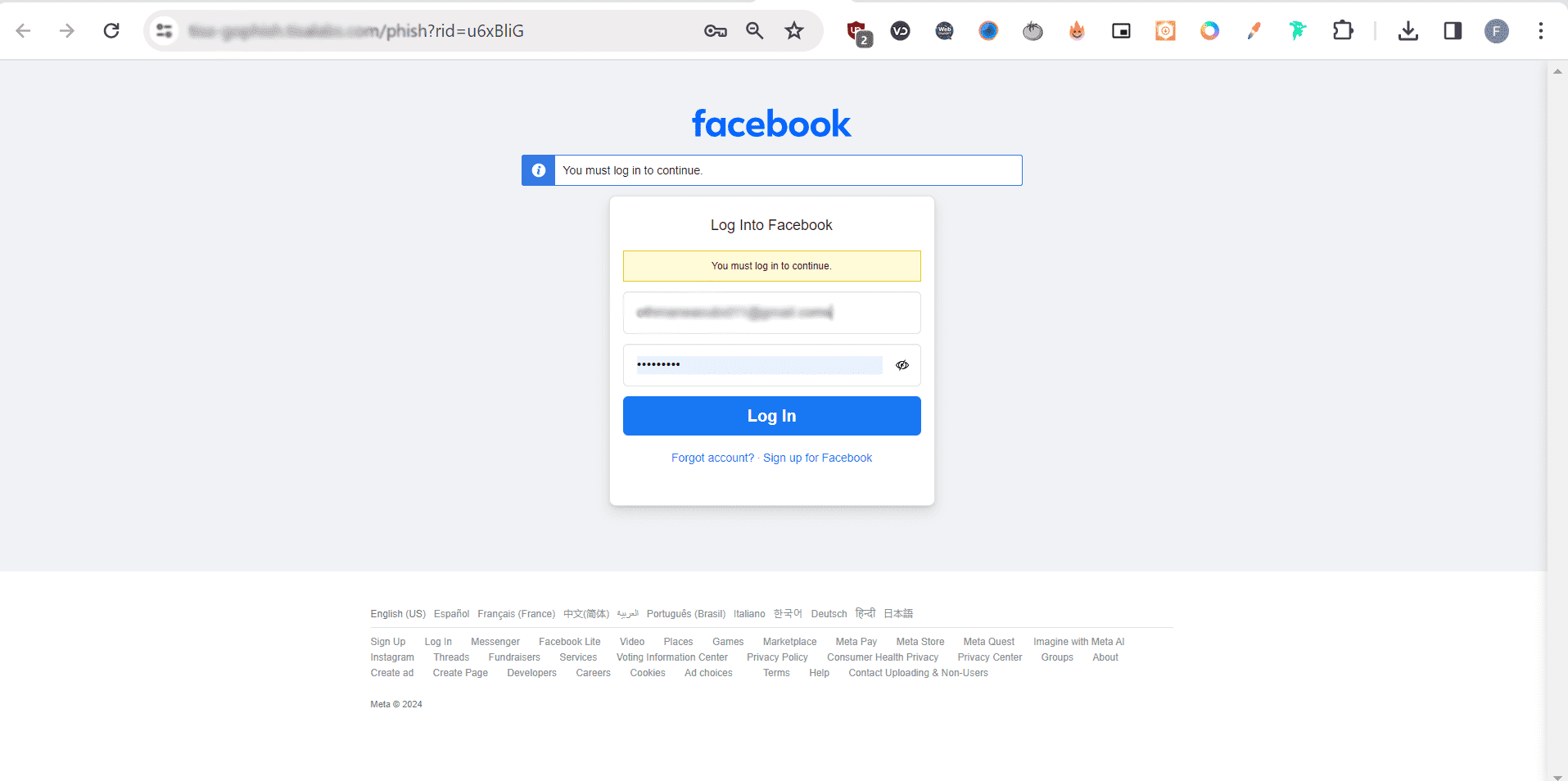
Step 3: Data Collection and Analysis Analysis of data collected from user interactions, including captured credentials, will be carried out to assess the campaign's success.
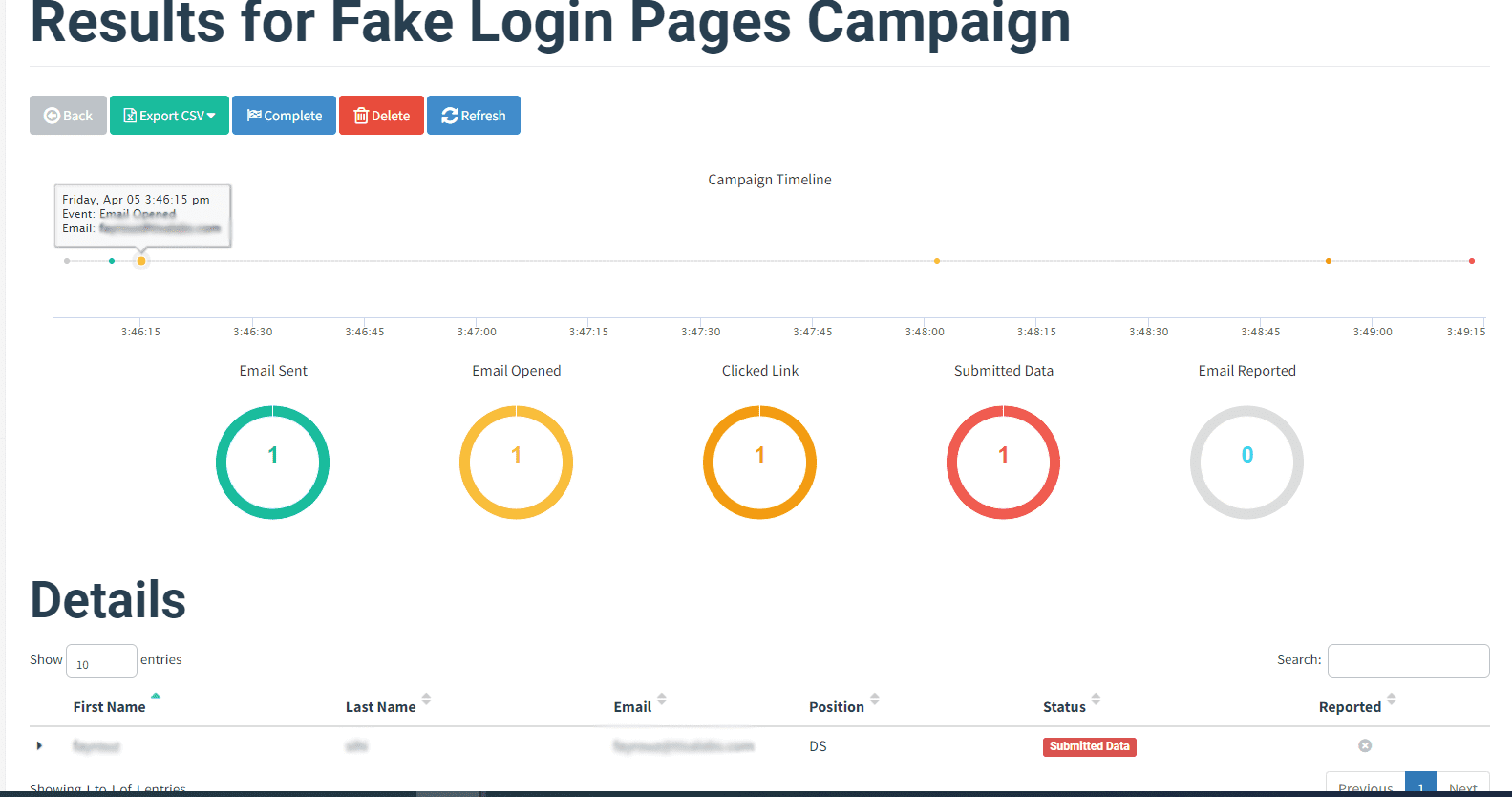
and These are the details of the data that we did capture from the fake login page:
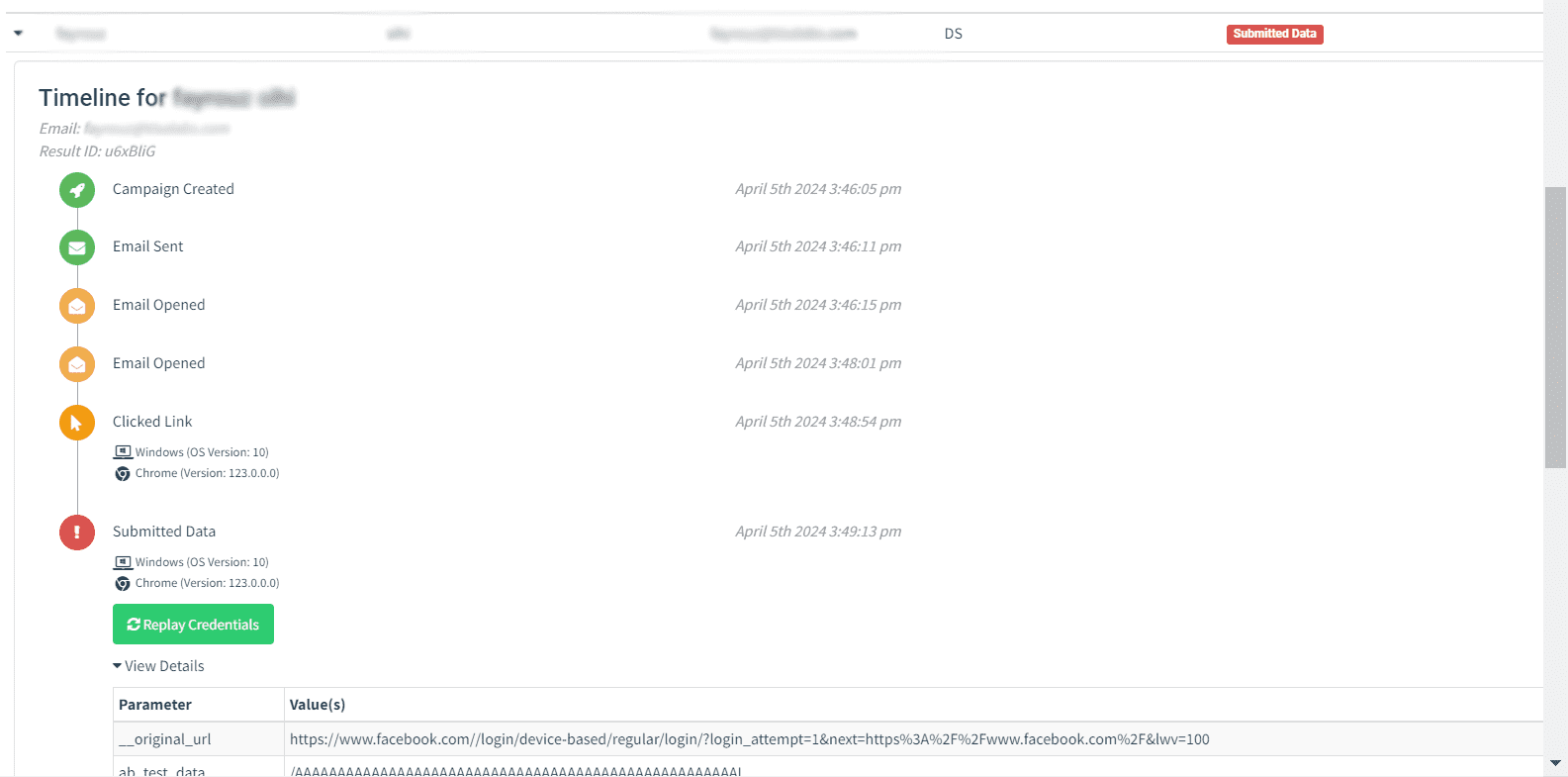
Execution of a phishing campaign featuring a fake login page provides valuable insights into organizational vulnerabilities. By following this tutorial, a better understanding of how to assess and mitigate risks effectively can be gained.
If you still can't find an answer to what you're looking for, or you have a specific question, open a new ticket and we'd be happy to help!
Contact Us